Have you ever heard of a hex dump? It’s a type of computer data analysis that you may not have heard of before, but it can be an invaluable tool in data security and computer forensics. In this article, we’ll explore what hex dumps are, how they work, and how to use them to find malicious code and other bad things.

What is a Hex/Hexadecimal
Hexadecimal, or “hex” for short, is a base-16 numbering system commonly used in computing and digital applications. It is similar to the base-10 system (decimal) that we are most familiar with, but instead of using 10 digits, hexadecimal uses 16 digits: 0,1,2,3,4,5,6,7,8,9,A,B,C,D,E and F. Each digit, or “hex digit,” represents a value ranging from 0 to 15. The letter A stands for 10, B for 11 and so on. When combined, hexadecimal digits can represent any number, letter, or combination of both. Hexadecimal is often used to represent colors, as each combination of hex digits can represent a specific color. It is also commonly used to represent binary data, such as files and images, as a more user-friendly way to read and communicate information.
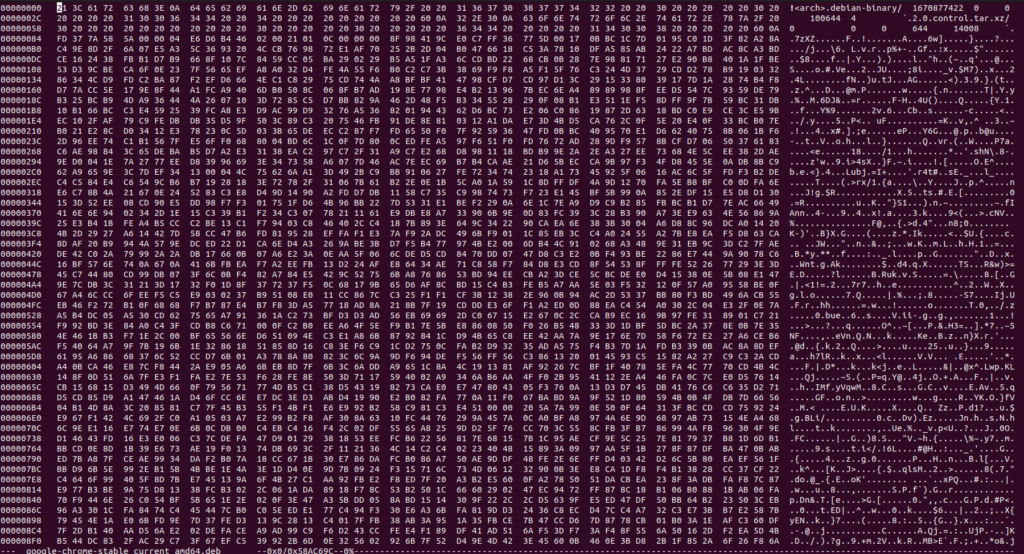
What is a Hex Dump?
A hex dump is a form of memory dump, which is a raw data representation of computer memory. It is usually displayed in hexadecimal form, which is a base 16 numerical system used to represent binary code. This can be useful for debugging, analyzing, and inspecting computer memory, as it is easier to read than raw binary code. The hex dump is also known as a hexadecimal value or hex editor.
How does a Hex Dump Work?
A hex dump works by converting computer memory into hexadecimal values. This is done by a process called byte-based conversion, which takes each byte of data and assigns it a hexadecimal value. This allows the hex dump to be more easily interpreted and edited than raw binary code.

What Can You Find with a Hex Dump?
Hex dumps can be used to find a variety of things, including malicious code, network packet data, and other bad things. By inspecting the hexadecimal values, you can quickly identify patterns and anomalies that could indicate malicious activity. Hex dumps can also be used to debug and inspect computer memory, as well as to inspect binary files.
How to Analyze Hex Dumps
Analyzing a hex dump can be a tricky task, as it requires a lot of knowledge and experience. It is important to understand the hexadecimal values and how they relate to the underlying data in order to accurately interpret a hex dump. Additionally, it is important to be familiar with the various types of data that can be found in a hex dump, such as executable files, network packet data, and memory dumps.
Tools for Hex Dump Analysis
There are a number of tools available to help with hex dump analysis. Hex editors are one of the most common tools used for this purpose, as they allow you to view and edit the hexadecimal values. Additionally, there are a number of other tools that can be used to analyze hex dumps, such as debuggers, disassemblers, and analyzers.
How are Hex Dumps used in Security?
Hex dumps are used to analyze binary data, such as malware, to determine its purpose, source, and effects. They can also be used to identify malicious code. By analyzing the hex dump of a file, security professionals can identify malicious code, as well as any other irregularities in the file. Furthermore, hex dumps can be used to debug applications and to detect errors in the data. Hex dumps can also be used to detect unauthorized changes to files, as well as to trace system calls. In short, hex dumps are a very useful tool for security professionals, as they can provide valuable insight into the data stored in a system.
Conclusion – Hex Dumps
Hex dumps can be a powerful tool in data security and computer forensics. By understanding what hex dumps are and how they work, you can use them to analyze computer memory and find malicious code. Additionally, there are a number of tools available to help with hex dump analysis, such as hex editors, debuggers, disassemblers, and analyzers. With the right tools and knowledge, you can use hex dumps to ensure the security of your data and networks.